c a l *
| vendor lock-in, security, & trust
february 21, 2016
Vendor lock-in refers to the dependency customers develop with a certain company, once they've bought enough products or services to make switching to a similar company's products or services prohibitively difficult or expensive. It applies throughout professions and industries ranging from photography to education to, perhaps most demonstrably, hardware and software design. Proprietary devices are a good concrete example of this - that cable and charger you bought for your Sony camera or your iPhone isn't going to cut it with a Canon or a Galaxy.
It's a little fuzzier explaining how vendor lock-in shapes behavior and usage expectations, but think about anything you're used to using - a computer program, a car, a musical instrument, a phone - and how weird it is if you ever have to use a version of the thing that's similar, but not yours, or not the one you're most familiar with. If you're used to driving a car where the gear shift is attached to the steering column but your rental for the weekend has one near the floor between the front seats, it feels strange. If you're an Android user and your friend wants you to take a photo of him with his iPhone, you might feel like you know what you're doing but also slightly off. The action you'd normally take to get back to the home screen could just take another photo, and you'll feel momentarily helpless as you get your legs (or more accurately, your fingertips) under you with this ever-so-slightly unfamiliar device.
Companies are wise to this phenomenon, though, and they know it impacts a person's decision to buy or not buy a given product; this is part of the reason why there's such a powerful tendency toward standardization among devices, programs, and products. Think about how many search engines - and really, not just standalone providers, but search bar functionality in general - mimic the simplicity of Google's standalone box:

From the perspective of a Google competitor, the rationale is pretty easy to see; it goes beyond simple copycatting. When you're aware of the reasons why your competitor gets the lion's share of the business - ease of use, legacy, prominence - you know there's no real sense or money in reinventing the successful wheel, and even if you can't go head-to-head on popularity or market share, you can control the interface and intended experience.
This does sometimes lead to infringement trouble for manufacturers (remember Samsung's loss to Apple?), but overall it's a wise tactic. When people are deciding to make major purchases like smartphones, computers, or cars, they typically won't respond well to an item or service that requires them to throw down a wad of cash and also forget everything they've ever known about using that item or service in the past. Better to keep user experience and expectations on an even keel as much as can be done, so as not to deter new potential customers or converts from making the already complicated switch to a different brand.
If Volvo decided to only build cars with steering controlled by a touchscreen console on the roof above the driver's seat, for instance, they'd alienate all but the most open-minded (or absurdly wealthy) consumers; everybody else in the market for a new vehicle would pick from the dozens of other car companies that still go with steering wheels. That's outlandish for sure, but it's also why radical innovations tend not to make much money for their inventors, and why incremental changes often amount to increased standardization. During the past decade, Microsoft has slowly molded Windows into a much more OS X-like experience. More and more cars use a "start/stop" button to turn on the engine. Phones, which not that long ago came in all shapes and sizes and colors, are now mostly rectangular touchscreens with a single button somewhere near the center bottom.

The reason why I bring any of this up is that I've been reading and listening to various stories and opinions about the FBI's demand that Apple build software that would allow them to unlock the San Bernardino gunman's iPhone. I don't own an iPhone, but the clear majority of my smartphone-owning friends and coworkers does; I'd say it's close to 90% of those folks. I also don't profess to be an infosec or tech expert of any sort, but it seems to me that a) the consequences of whatever decision is reached in this case are going to be far-reaching, and b) that most people who own iPhones have next to no idea how they work, what makes them work and what keeps them safe, and who is responsible for their security.
How many people make a decision to buy an iPhone because it has a cryptographic key that is "generated by combining the user's passcode with a key baked in to the hardware in a way that is designed to be difficult to extract?" How many people know the passcode they choose is a factor in their iPhone's encryption system, or that their iPhone is encrypted in the first place? And how many associate encryption with the evildoers and terrorists that are invoked every time a government agency puts pressure on a tech company for a backdoor (or whenever a presidential candidate is asked about digital rights)?
I'd guess the average iPhone user has an iPhone because everybody else in their friend or family circle does, or because their employer gave it to them, or because, I dunno, they like the form factor. Most people probably assume their phones and the activities they use them for are safe and secure because they were promised as much at the Apple Store, or because they're long-term Apple fans, or because their acquaintances with iPhones have never had any complaints about hacking or identity theft or what-have-you. If people give much of a thought to security at all, I'm guessing a chunk of them may put their faith in Apple more or less completely, not only because they haven't had any problems personally but because it's easier to believe there's nothing to worry about. Maybe I'm shooting in the dark here, but I don't think strong encryption or the idea of a secure enclave has much of an impact on their continued iPhone use.
Combine that unwaivering faith in Apple-slash-wisdom of the crowd (or maybe it's jaded acceptance that we'll all be compromised sooner or later; see below) with the amount of activities and content and functionality users have come to depend on their iPhones for, and it's tough to imagine many of those users wanting to switch to another device. Add in the familiarity and ease of use that comes with touching and holding and interacting with the same (or a very similar) device for years, and it becomes even harder to imagine a changeup.
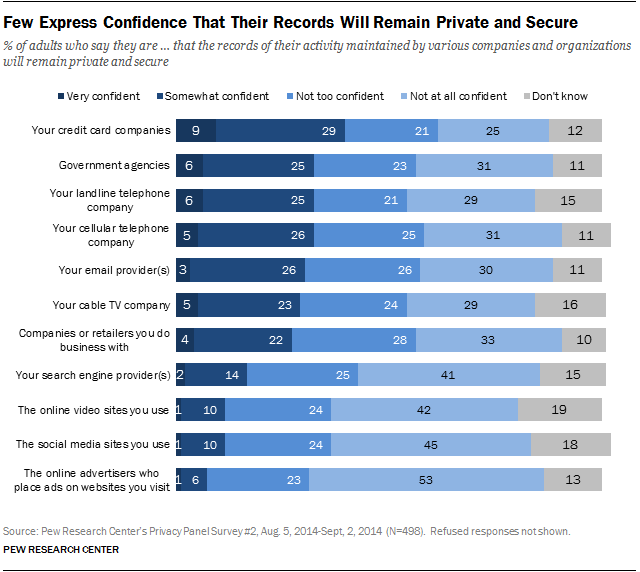
When you consider the amount of things we handle from the comfort of our smartphones - finding directions, managing bank accounts, ordering food, checking email, making notes to ourselves, documenting our daily lives through photo and video - it's staggering how much influence one company can have in the lives of its customers, just through one device. It's a degree of vendor lock-in that no proprietary data cable could have prepared us for a decade ago because no single device at that time - at least not one with anywhere near the prevalence and power of the present-day smartphone - had a role in so many facets of a person's life.
So far, Apple is battling this request for "FBiOS" with what overwhelmingly seems like good reason, despite the less-than-positive prognosis for the outcome of that fight. Maybe the media attention the case is getting will shed some light on the dim corridors of encryption and info security that are all too easy to ignore or misunderstand. But people could do worse than to dig deeper into the security features of their devices (or the lack thereof), to learn what mechanisms are in place to protect users, such as encryption - and that's not just aimed at iPhone users. Just the opposite: many Android phones require manual setup for encryption, use language that deters users from doing it, and don't natively require passcodes. Either way, given the trajectory toward dependence on these devices, it's a new literacy many would stand to benefit from.
Vendor lock-in is frighteningly all-encompassing these days. Phone manufacturers are just the tip of the iceberg, too; consider the reliance folks have on cloud services and tools like Dropbox and Google Drive, not even to get into things like proprietary file formats. But if we're going to steadfastly stick by our choice of company for plugging us into the necessities (or, well, features) of 21st century life - plus also trust that company to protect our secrets, our messages, our bank accounts, and the constant documentation-stream of our lives - the least we could do is try to understand why.
home | top
Hey Cal, why is there no comments section? Comments sections have a tendency to devolve into nasty little spaces, teeming with spam & ad hominem attacks. I also have a fondness for the 1.0 Web (props to Neocities, powerer of this site). If you'd like to share your thoughts, find me on Twitter or fire off an email. Thanks!